Sophisticated Malvertising Campaigns Exploit Google Ads to Distribute Targeted Malware
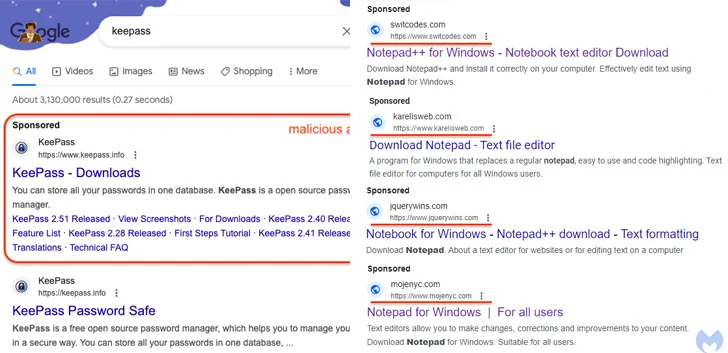
Details have surfaced about a sophisticated malvertising campaign utilizing Google Ads to deceive users searching for popular software. Uncovered by Malwarebytes, the campaign involves redirecting users seeking Notepad++ and PDF converters to fake landing pages, where decoy ads are displayed. Upon interaction, the visitor's system is silently fingerprinted to identify virtual machines. If the user is deemed a potential target, they are redirected to a replica website advertising the software, assigned a unique ID for tracking, and served a time-sensitive malware payload. The final-stage malware establishes a connection to a remote domain, delivering subsequent malicious payloads. Jérôme Segura, Director of Threat Intelligence, highlights the success of threat actors in evading ad verification checks, allowing for targeted attacks. A parallel campaign targets users searching for the KeePass password manager, using malicious ads and Punycode to deceive victims into downloading malware. This combination of Punycode and rogue Google Ads reflects an increased sophistication in malvertising via search engines. Additionally, various threat actors are exploiting fake browser updates to propagate Cobalt Strike, loaders, stealers, and remote access trojans. This tactic involves abusing end-user trust with compromised websites and personalized lures, emphasizing the constant evolution of these visual trickery-based attacks. The findings underscore the growing complexity of malvertising techniques and the need for enhanced cybersecurity measures.